Category: Publications
-

Wearable technology: Big companies get involved in Big Brother-style monitoring of staff
A nice article (that our researcher Lee Tobin contributed to) in The Irish Times newspaper on how wearable technology might impact our working lives. Here is an excerpt: ” …Wearable technologies are nothing new. The Google Glass consumer-oriented product allows owners to do many of the things they could do on their tablet with a pair…
-

An Argument for Assumed Extra-territorial Consent During Cybercrime Investigations
During cybercrime investigations it’s common to find that a suspect has used technology in a country outside of the territorial jurisdiction of Law Enforcement investigating the case. The suspects themselves may also be located outside of the territory of the investigating group. A country may be able to claim jurisdiction over a suspect or device…
-
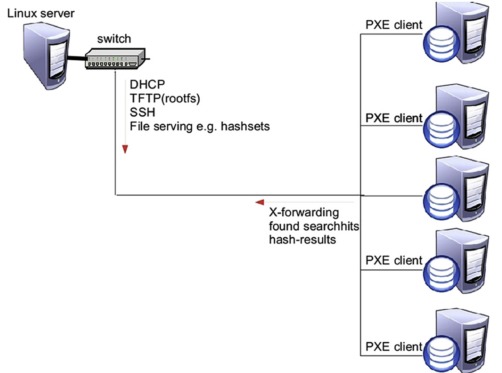
Automated Network Traige
In many police investigations today, computer systems are somehow involved. The number and capacity of computer systems needing to be seized and examined is increasing, and in some cases it may be necessary to quickly find a single computer system within a large number of computers in a network. To investigate potential evidence from a…
-

Digital Forensic Investigation and Cloud Computing
Earlier this year, researchers from the Digital Forensic Investigation Research Group had a chapter published in the book “Cybercrime and Cloud Forensics: Applications for Investigation Processes“. There were contributions from authors discussing practical as well as theoretical aspects of digital crime, investigation, side channel attacks, law, international cooperation, and the future of crime and Cloud…
-

Signature Based Detection of User Events for Post-Mortem Forensic Analysis
The concept of signatures is used in many fields, normally for the detection of some sort of pattern. For example, antivirus and network intrusion detection systems sometimes implement signature matching to attempt to differentiate legitimate code or network traffic from malicious data. The principle of these systems that that within a given set of data, malicious data…
-

Evasion-Resistant Malware Signature Based on Profiling Kernel Data Structure Objects
Malware creators are continually looking for new methods to evade malware detection engines. A popular evasion method is based on malicious code obfuscation that changes the syntax of the code while preserving its execution semantics. If the malware signature relies on the syntactic features of the malicious code, it can be evaded by obfuscation techniques. In this…
-
Towards Automated Forensic Event Reconstruction of Malicious Code
Many existing methods of forensic malware analysis rely on the investigators’ practical experience rather than hard science. This paper presents a formal (i.e. based on mathematics) approach to reconstructing activities of a malicious executable found in a victim’s system during a post-mortem analysis. The behavior of the suspect executable is modeled as a finite state automaton where…
-
A Novel Methodology for Malware Intrusion Attack Path Reconstruction
When a malware outbreak happens in an organization, one of the main questions that needs to be investigated is how the malware got in. It is important to get an answer to this question to identify and close the exploited technical and/or human vulnerabilities. This paper proposes a method for malware intrusion path reconstruction in a…
-
Automata Intersection to Test Possibility of Statements in Investigations
When conducting an investigation, many statements are given by witnesses and suspects. A “witness” could be considered as anything that provides information about the occurrence of an event. While a witness may traditionally be a human, a digital device – such as a computer or cell phone – could also help to provide information about…