Category: Computer Forensics
-

Open Forensic Devices
Cybercrime has been a growing concern for the past two decades. What used to be the responsibility of specialist national police has become routine work for regional and district police. Unfortunately, funding for law enforcement agencies is not growing as fast as the amount of digital evidence. In this paper, we present a forensic platform…
-
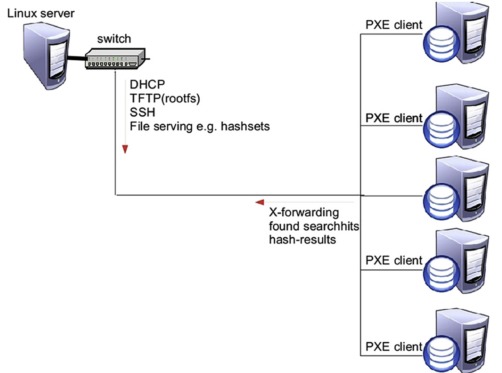
Automated Network Traige
In many police investigations today, computer systems are somehow involved. The number and capacity of computer systems needing to be seized and examined is increasing, and in some cases it may be necessary to quickly find a single computer system within a large number of computers in a network. To investigate potential evidence from a…
-

Digital Forensic Investigation and Cloud Computing
Earlier this year, researchers from the Digital Forensic Investigation Research Group had a chapter published in the book “Cybercrime and Cloud Forensics: Applications for Investigation Processes“. There were contributions from authors discussing practical as well as theoretical aspects of digital crime, investigation, side channel attacks, law, international cooperation, and the future of crime and Cloud…
-
Some Pitfalls of Interpreting Forensic Artifacts in Windows Registry
This post is on behalf of one of our students, Ms. Jacky Fox. Given below is the archive that contains her MSc dissertation and the Bash scripts she wrote to extract and correlate Windows registry artifacts. During her research she discovered that recent versions of Microsoft Windows introduced subtle changes to forensic interpretation of Windows…
-
Report of digital forensic standards, processes and accuracy measurement
From December 7th 2010 to December 12th 2010 a survey on Digital Investigation Process and Accuracy was conducted in an attempt to determine the current state of digital investigations, the process of examination (examination phases), and how those examinations are being verified as accurate. An online survey was created in English, and consisted of 10…
-
Survey of Evidence and Forensic Tool Usage in Digital Investigations
This work is in regards to a 2009 project about research into real-world digital forensic practices for the development of highly automated tools to increase speed and efficiency of forensic investigations. A survey was conducted of 30 Law Enforcement officers from different countries in Europe (with 10 respondents). The key findings of the survey are given,…