SAN or Storage Area Network is one of the vital components in the Cloud and performing digital forensics Cloud storage is so challenging not only because of the size but also the technology involved. The two main SAN types in the market are fiber channel and iSCSI. There are many different SAN vendors in the market, including but not limited to NetApp, Hitachi, EMC, Dell, HP etc. In this post I would like focus on the EMC platform.
A better parallel operation or process needs to occur so evidence that is important to the investigation is collected first while keeping the client’s business running throughout the investigation. This need to occur without impacting business downtime due to technical difficulties that could lead client’s to lose millions of dollars.
In practical world, acquiring evidence of the entire cloud storage system may not be required. If there is a fraud investigation involving a single individual, then it is not practical or necessary to image 20 terabytes of storage that might contains other client’s sensitive data which is not relevant to the case. It is more efficient to triage the area that the individual had access, and image only that relevant data. The good news about SAN in private cloud is that it is divided into logical unit numbers (LUN). If relevant evidence/data is located in single system then the LUN assigned to that particular system may be only piece of the SAN that needs to be acquired.
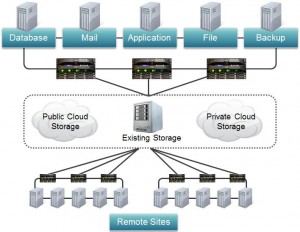
It may be difficult for computer forensic investigator to know where to start when facing the situation alike in the figure shown below. However, with an existing solid foundation of storage technology, combined with a solid forensic background, one can overcome these concerns and perform a sound forensic investigation that holds up to legal challenge.
There are several different methods that can be utilized in capturing a forensically sound image of private cloud storage that a host may be using. Each comes with pros and cons and should be considered in view of the ultimate goal of the forensic investigation.
- Adding new host to existing SAN environment that involve bringing new computer system on site to capture the data.
- Using existing host in SAN with preferred forensic tools from a trusted CD mounted by the host to capture data from the storage enclosure.
- Clone or replicate the LUN to different enclosure in the SAN and adding new host to different logical group with new LUN to capture the image.
Above listed are the few methods that can be utilized and details of each method will be discussed in my next blog. I hope you enjoyed the post and feel free to contact me if you have any comments or anything you would like to see.


Leave a Reply